Networking Interview Questions
IMPORTANT NETWORKING INTERVIEW QUESTIONS AND ANSWERS
Table of contents
- Basic Networking Interview Questions
- 1. What is the network?
- 2. Explain different types of networks.
- 3. Explain LAN (Local Area Network)
- 4. What is VPN (Virtual Private Network) and What are the advantages of using a VPN?
- 5. What is the network topology? Define different types of network topology
- 6. What is an IPv4 address? What are the different classes of IPv4?
- 7. What are Private and Special IP addresses?
- 8. What are the different types of VPNs?
- 9. What are nodes and links?
- Intermediate Interview Questions
- 1. Describe the OSI Reference Model
- 2. Define the 7 different layers of the OSI Reference Model
- 3. Describe the TCP/IP Reference Model
- 4. Define the 4 different layers of the TCP/IP Reference Model
- 5. Differentiate OSI Reference Model And TCP/IP Reference Model
- 6. What are the HTTP and the HTTPS protocol?
- 7. What is the SMTP protocol?
- 8. What is DNS?
- 9. What is the use of a router and how is it different from a gateway?
- Advanced Interview Questions
- 1. What is the TCP protocol?
- 2. What is the UDP protocol?
- 3. Compare TCP and UDP
- 4. What is the ICMP protocol?
- 5. What do you mean by the DHCP Protocol?
- 6. What is the ARP protocol?
- 7. What is the FTP protocol?
- 8. What is the MAC address and how is it related to NIC?
- 9. Differentiate the MAC address from the IP address
- 10. What is a subnet?
- 11. Compare the hub vs switch
- 12. What is the difference between the ipconfig and the ifconfig?
- 13. What is the firewall?
- 14. What are Unicasting, Anycasting, Multicasting and Broadcasting?
- 15. What happens when you enter google.com in the web browser?
- Conclusion
Basic Networking Interview Questions
1. What is the network?
A network is usually an informally interconnected group or association of different entities like a person, computers, radio stations, etc.
For example, Dominos has a network of 1232 branches across India. As the name suggests the computer network is a system of peripherals or computers interconnected with each other and has a standard communication channel established between them to exchange different types of information and data.
2. Explain different types of networks.
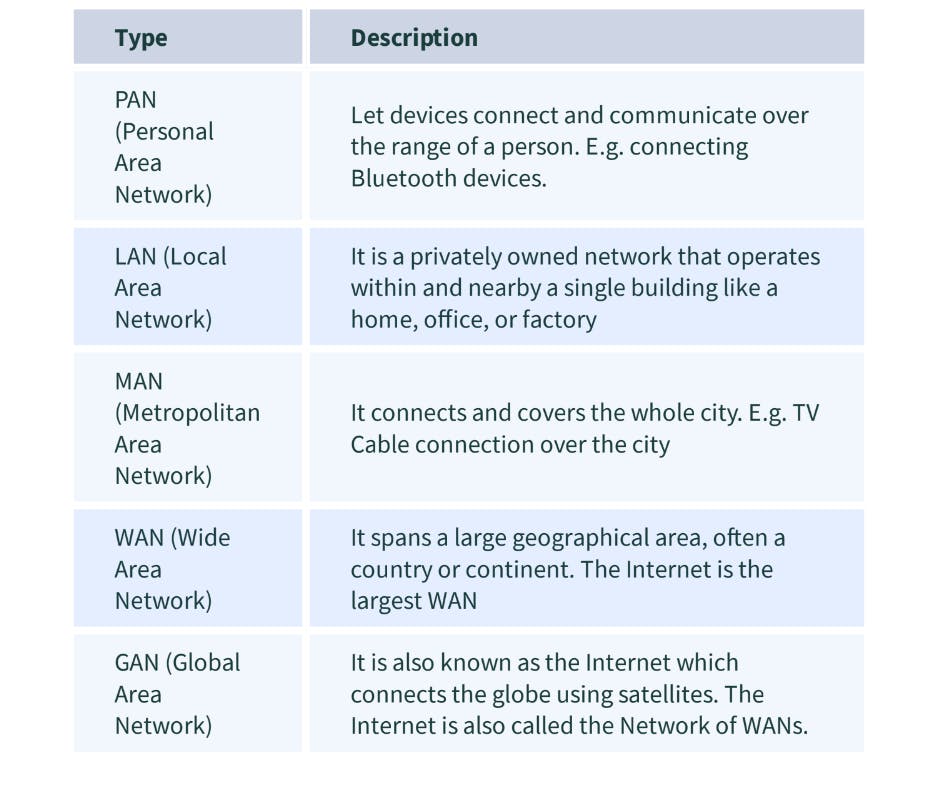
3. Explain LAN (Local Area Network)
LANs are widely used to connect computers/laptops and consumer electronics which enables them to share resources (e.g., printers, fax machines) and exchange information. When LANs are used by companies or organizations, they are called enterprise networks. There are two different types of LAN networks i.e. wireless LAN (no wires involved achieved using Wi-Fi) and wired LAN (achieved using LAN cable). Wireless LANs are very popular these days for places where installing wire is difficult. The below diagrams explain both wireless and wired LAN.
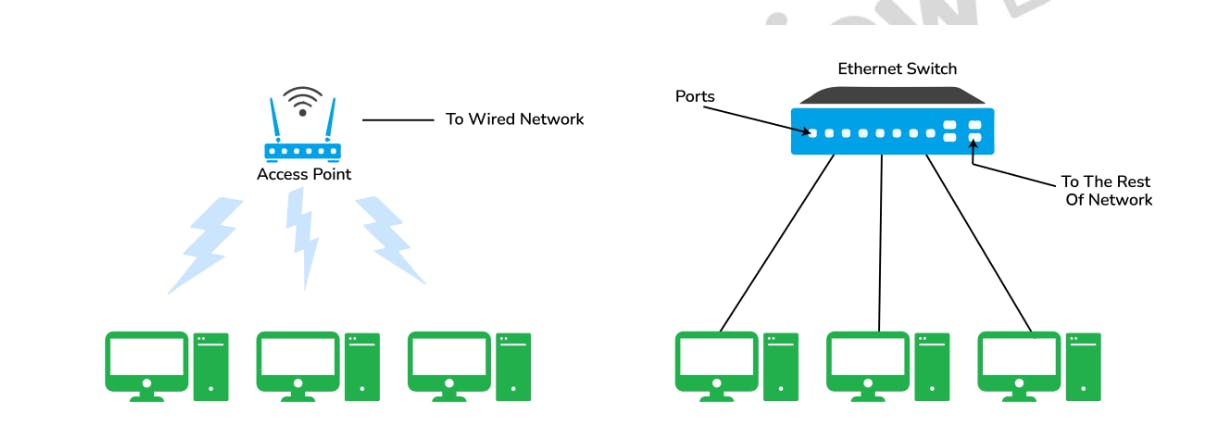
4. What is VPN (Virtual Private Network) and What are the advantages of using a VPN?
VPN or the Virtual Private Network is a private WAN (Wide Area Network) built on the internet. It allows the creation of a secured tunnel (protected network) between different networks using the internet (public network). By using the VPN, a client can connect to the organization’s network remotely.
Below are a few advantages of using a VPN:
VPN is used to connect offices in different geographical locations remotely and is cheaper when compared to WAN connections.
VPN is used for secure transactions and confidential data transfer between multiple offices located in different geographical locations.
VPN keeps an organization’s information secured against any potential threats or intrusions by using virtualization.
VPN encrypts the internet traffic and disguises the online identity.
5. What is the network topology? Define different types of network topology
Network topology is a physical layout of the network, connecting the different nodes using the links. It depicts the connectivity between the computers, devices, cables, etc.
The different types of network topology are:
Bus Topology:
All the nodes are connected using the central link known as the bus.
It is useful to connect a smaller number of devices.
If the main cable gets damaged, it will damage the whole network.
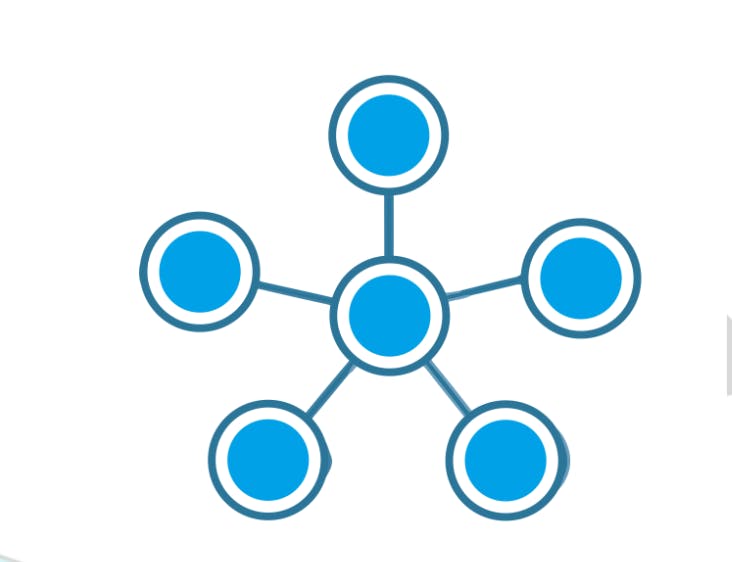
Star Topology:
All the nodes are connected to one single node known as the central node.
It is more robust.
If the central node fails the complete network is damaged.
Easy to troubleshoot.
Mainly used in home and office networks.
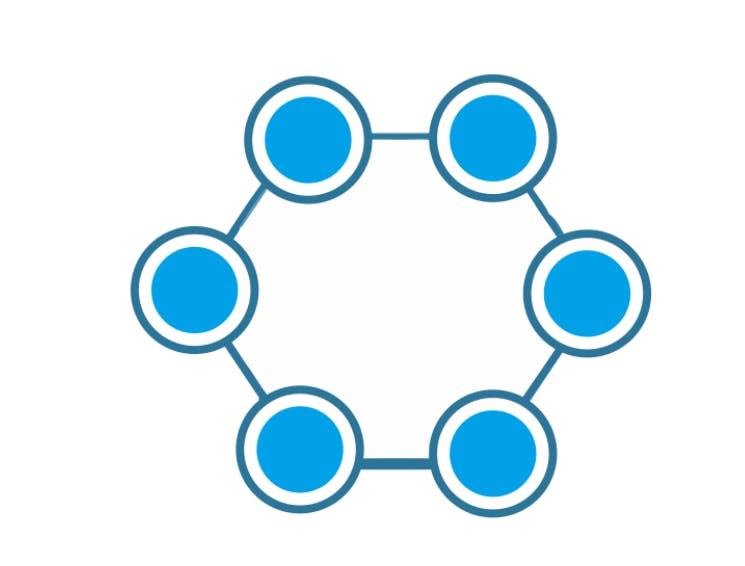
Ring Topology:
Each node is connected to exactly two nodes forming a ring structure.
If one of the nodes is damaged, it will damage the whole network.
It is used very rarely as it is expensive and hard to install and manage.
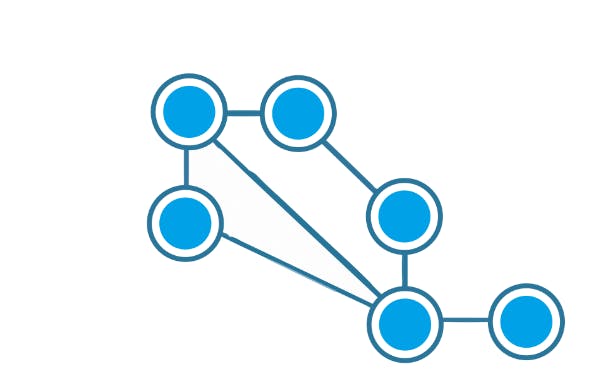
Mesh Topology:
Each node is connected to one or many nodes.
It is robust as failure in one link only disconnects that node.
It is rarely used and installation and management are difficult.
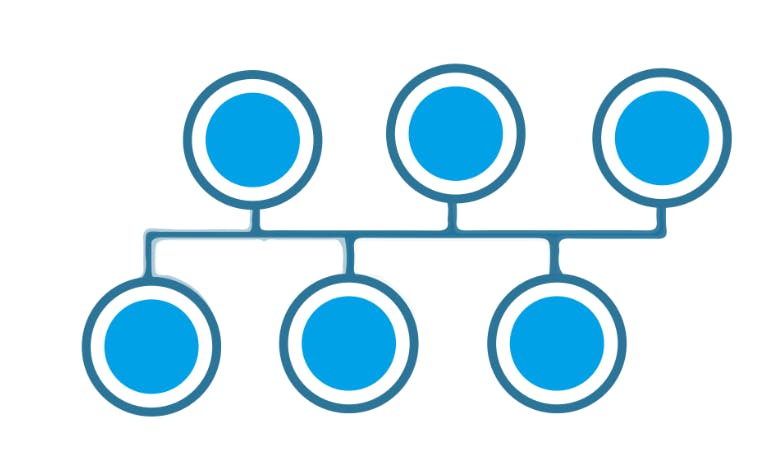
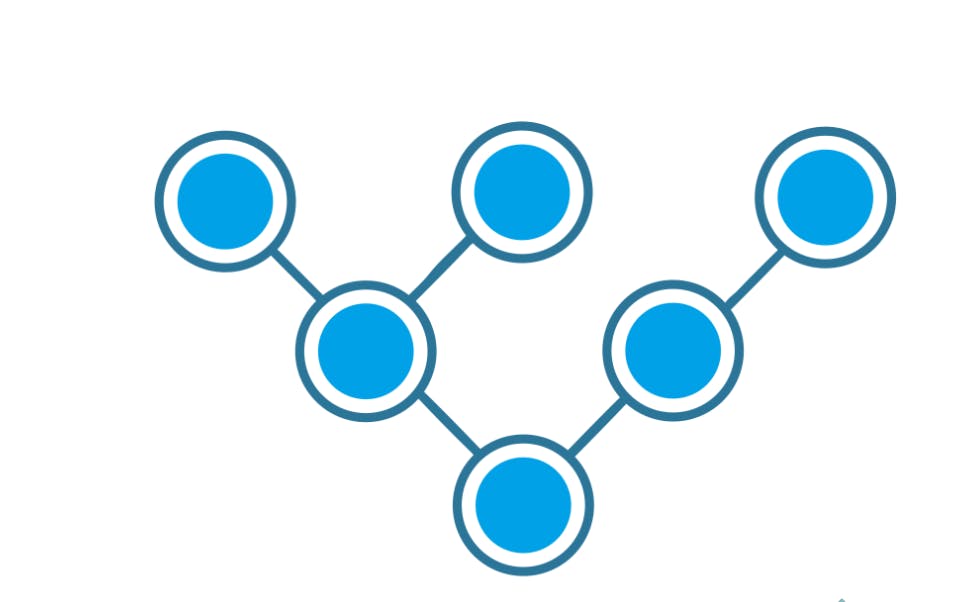
Tree Topology:
A combination of star and bus topology also know as an extended bus topology.
All the smaller star networks are connected to a single bus.
If the main bus fails, the whole network is damaged.
Hybrid:
It is a combination of different topologies to form a new topology.
It helps to ignore the drawback of a particular topology and helps to pick the strengths from others.
6. What is an IPv4 address? What are the different classes of IPv4?
An IP address is a 32-bit dynamic address of a node in the network. An IPv4 address has 4 octets of 8-bit each with each number with a value up to 255.
IPv4 classes are differentiated based on the number of hosts it supports on the network. There are five types of IPv4 classes and are based on the first octet of IP addresses which are classified as Class A, B, C, D, or E.
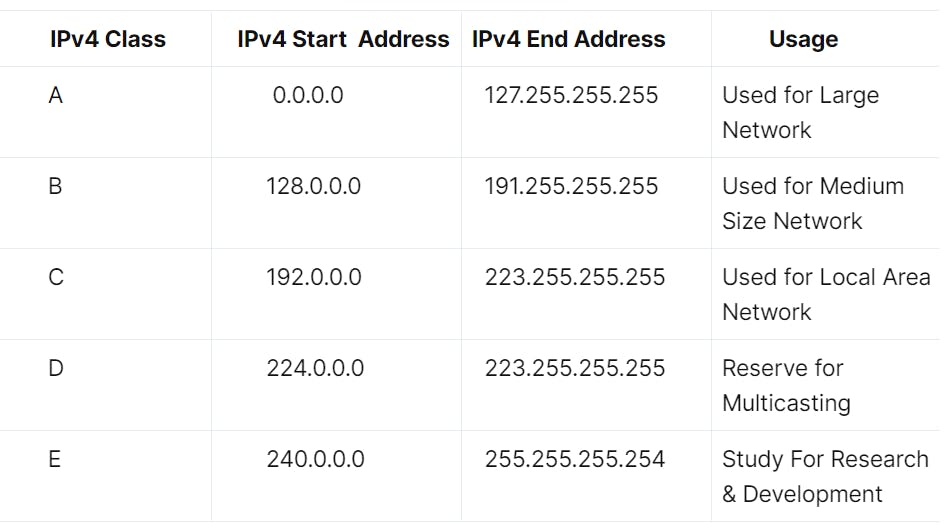
7. What are Private and Special IP addresses?
Private Address: For each class, there are specific IPs that are reserved specifically for private use only. This IP address cannot be used for devices on the Internet as they are non-routable.
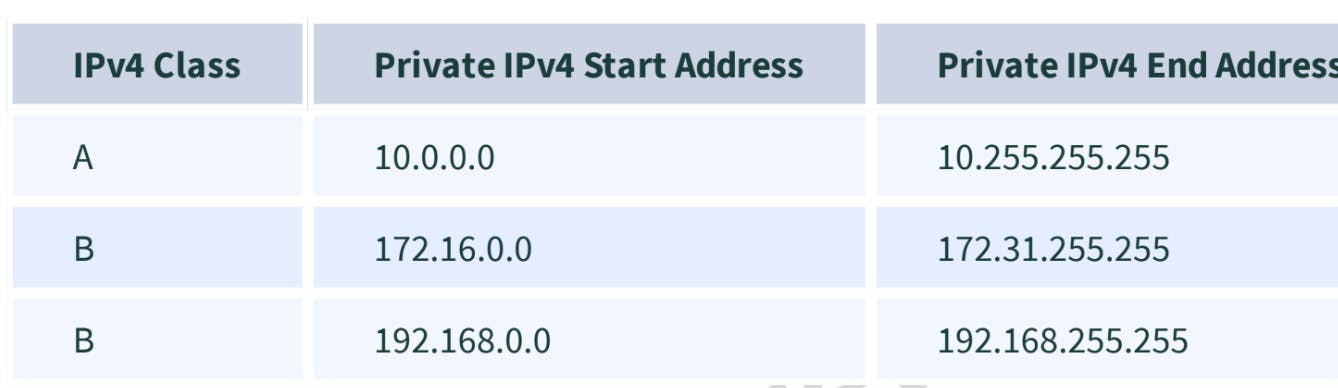
Special Address: IP Range from 127.0.0.1 to 127.255.255.255 are network testing addresses also known as loopback addresses are a special IP address.
8. What are the different types of VPNs?
A few types of VPNs are:
Access VPN: Access VPN is used to provide connectivity to remote mobile users and telecommuters. It serves as an alternative to dial-up connections or ISDN (Integrated Services Digital Network) connections. It is a low-cost solution and provides a wide range of connectivity.
Site-to-Site VPN: A Site-to-Site or Router-to-Router VPN is commonly used in large companies having branches in different locations to connect the network of one office to another in different locations. There are 2 sub-categories:
Intranet VPN: Intranet VPN is useful for connecting remote offices in different geographical locations using shared infrastructure (internet connectivity and servers) with the same accessibility policies as a private WAN (wide area network).
Extranet VPN: Extranet VPN uses shared infrastructure over an intranet, suppliers, customers, partners, and other entities and connects them using dedicated connections.
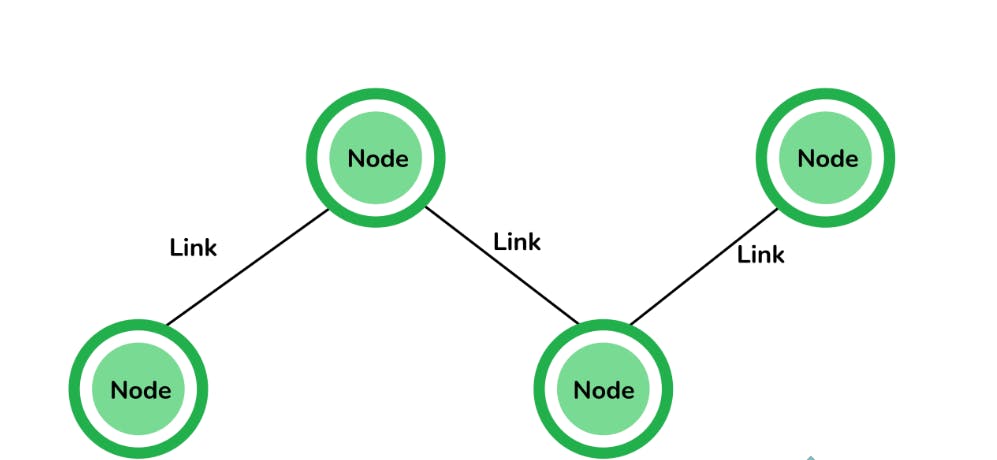
9. What are nodes and links?
Node: Any communicating device in a network is called a Node. The node is the point of intersection in a network. It can send/receive data and information within a network. Examples of the node can be computers, laptops, printers, servers, modems, etc.
Link: A link or edge refers to the connectivity between two nodes in the network. It includes the type of connectivity (wired or wireless) between the nodes and protocols used for one node to be able to communicate with the other.
Intermediate Interview Questions
1. Describe the OSI Reference Model
Open System Interconnections (OSI) is a network architecture model based on the ISO standards. It is called the OSI model as it deals with connecting the systems that are open for communication with other systems.
The OSI model has seven layers.
Create a new layer if a different abstraction is needed.
Each layer should have a well-defined function.
The function of each layer is chosen based on internationally standardized protocols.
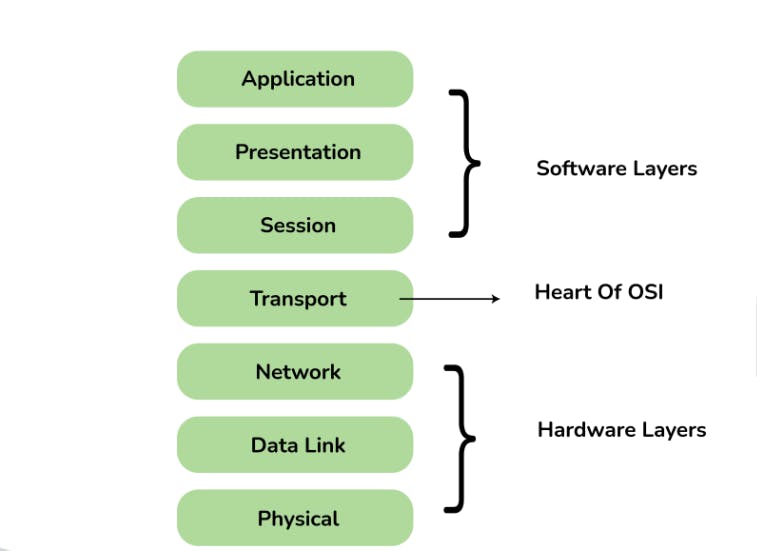
2. Define the 7 different layers of the OSI Reference Model
Here are the 7 layers of the OSI reference model:
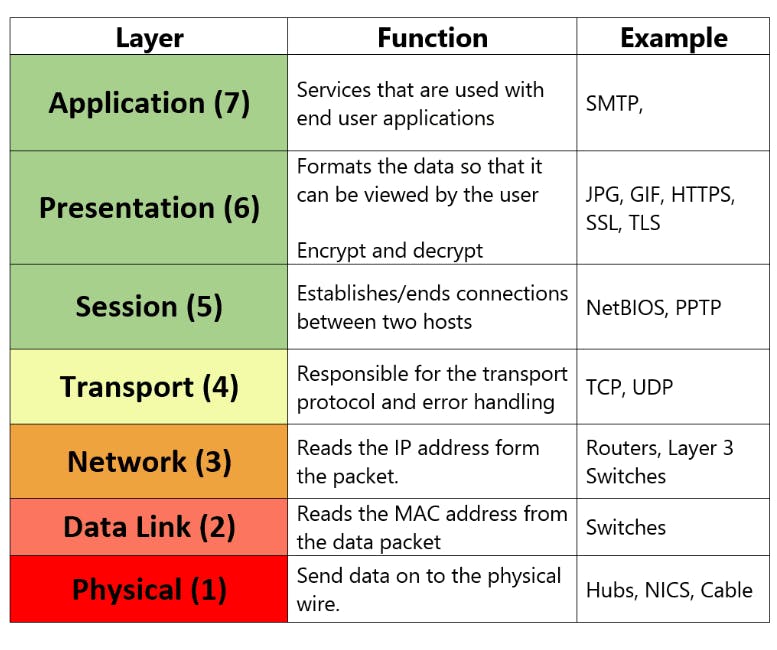
3. Describe the TCP/IP Reference Model
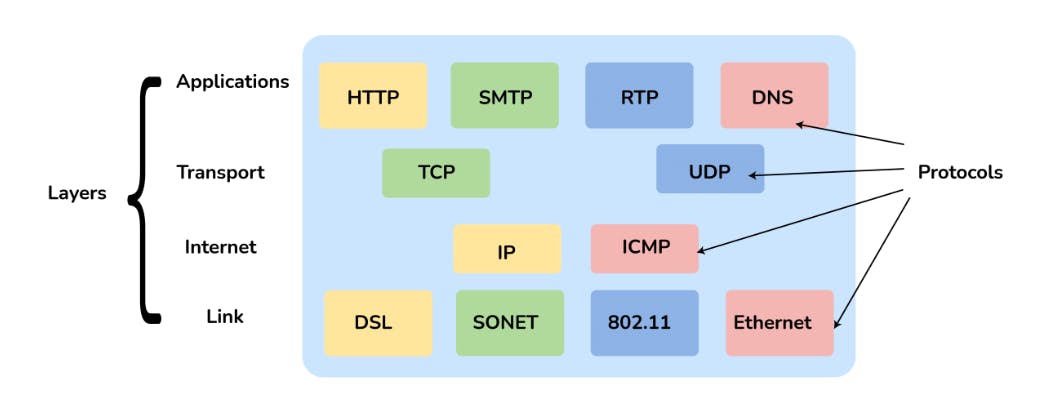
It is a compressed version of the OSI model with only 4 layers. It was developed by the US Department of Defence (DoD) in the 1860s. The name of this model is based on 2 standard protocols used i.e. TCP (Transmission Control Protocol) and IP (Internet Protocol).
4. Define the 4 different layers of the TCP/IP Reference Model
Layers | Description |
DataLink | Decides which links such as serial lines or classic Ethernet must be used to meet the needs of the connectionless internet layer. |
Internet | The internet layer is the most important layer which holds the whole architecture together. It delivers the IP packets where they are supposed to be delivered. |
Transport | Its functionality is almost the same as the OSI transport layer. It enables peer entities on the network to carry on a conversation. |
Application | It contains all the higher-level protocols. |
5. Differentiate OSI Reference Model And TCP/IP Reference Model
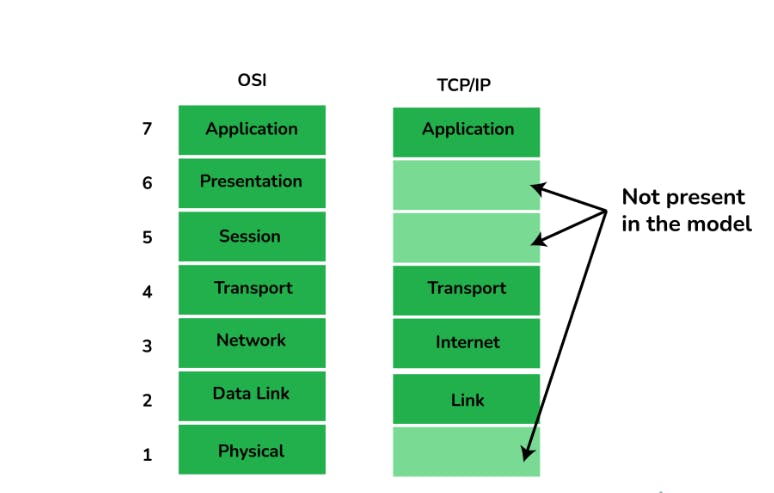
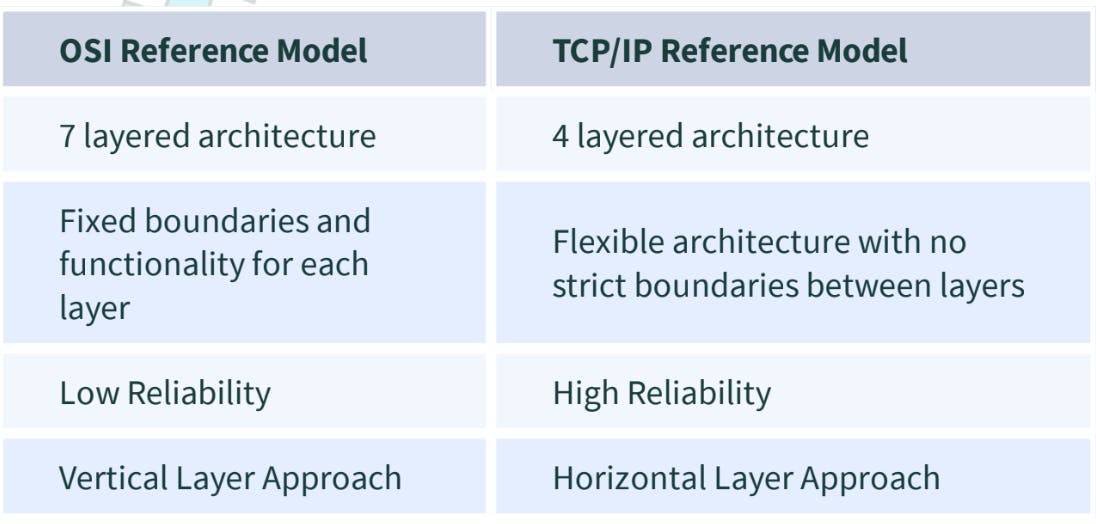
6. What are the HTTP and the HTTPS protocol?
HTTP is the HyperText Transfer Protocol which defines the set of rules and standards on how information can be transmitted on the World Wide Web (WWW). It helps web browsers and web servers communicate. It is a ‘stateless protocol’ where each command is independent of the previous command. HTTP is an application layer protocol built upon the TCP. It uses port 80 by default.
HTTPS is the HyperText Transfer Protocol Secure or Secure HTTP. It is an advanced and secure version of HTTP. On top of HTTP, SSL/TLS protocol is used to provide security. It enables secure transactions by encrypting communication and also helps identify network servers securely. It uses port 443 by default.
7. What is the SMTP protocol?
SMTP is the Simple Mail Transfer Protocol. SMTP sets the rule for communication between servers. This set of rules helps the software transmit emails over the internet. It supports both End-to-End and Store-and-Forward methods. It is in always-listening mode on port 25.
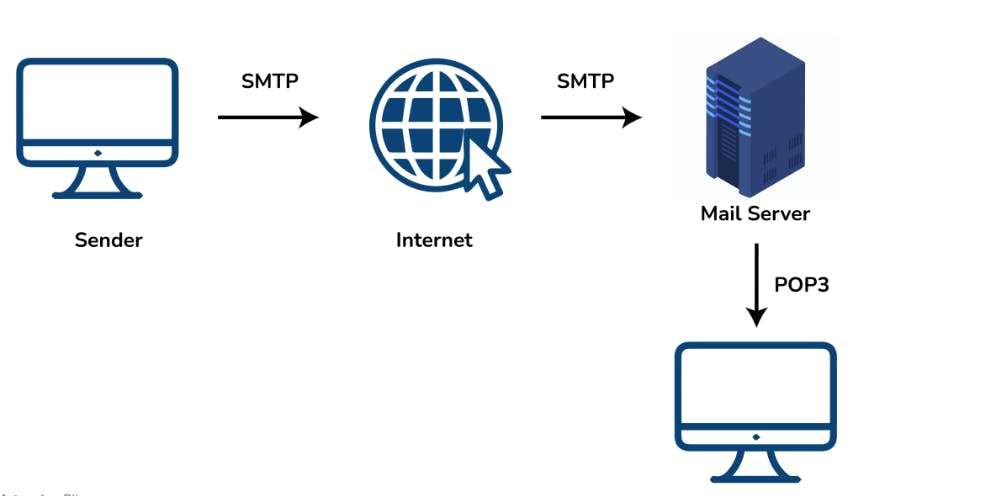
8. What is DNS?
DNS is the Domain Name System. It is considered the devices/services directory of the Internet. It is a decentralized and hierarchical naming system for devices/services connected to the Internet. It translates the domain names to their corresponding IPs. For e.g. BiswajitMohapatra.com to 172.217.164.16. It uses port 53 by default.
9. What is the use of a router and how is it different from a gateway?
The router is a networking device used for connecting two or more network segments. It directs the traffic in the network. It transfers information and data like web pages, emails, images, videos, etc. from source to destination in the form of packets. It operates at the network layer. The gateways are also used to route and regulate the network traffic but, they can also send data between two dissimilar networks while a router can only send data to similar networks.
Advanced Interview Questions
1. What is the TCP protocol?
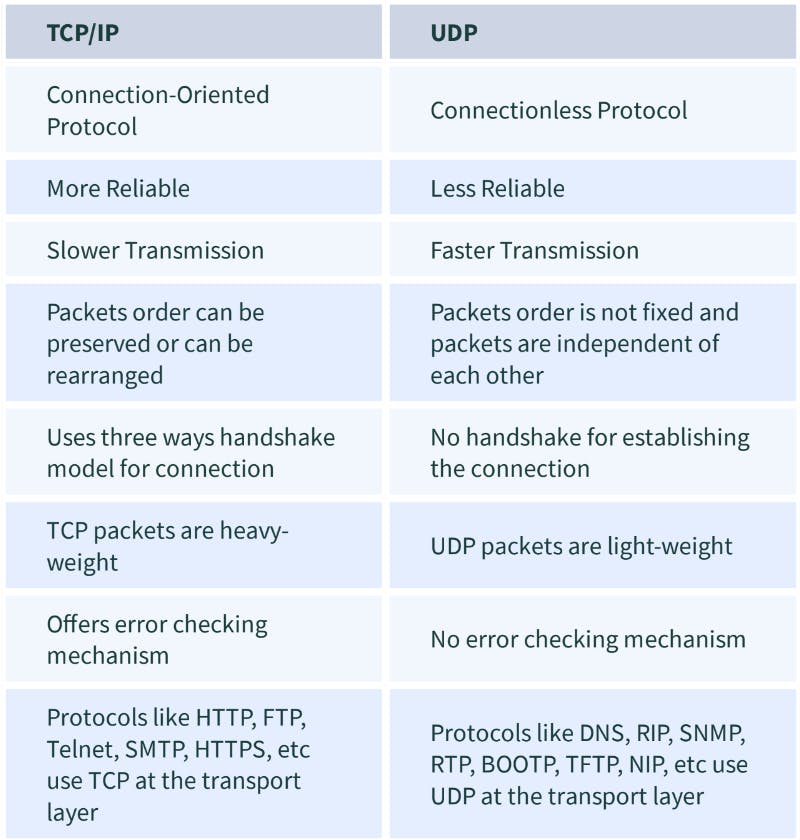
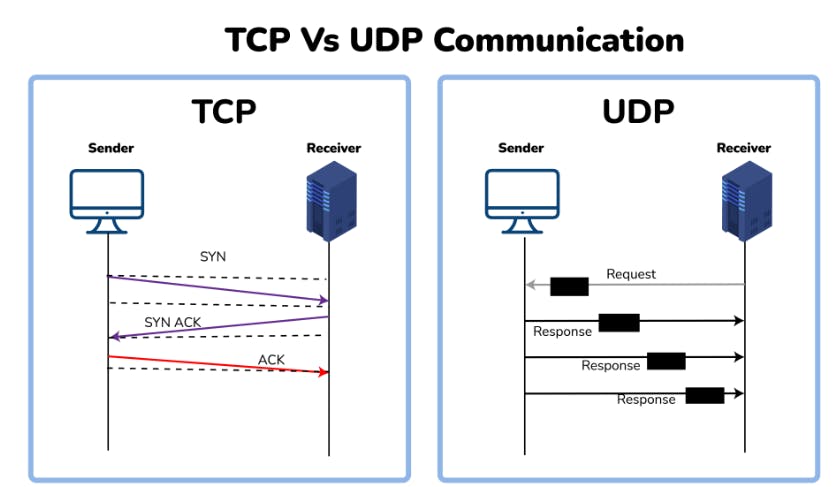
TCP or TCP/IP is the Transmission Control Protocol/Internet Protocol. It is a set of rules that decides how a computer connects to the Internet and how to transmit the data over the network. It creates a virtual network when more than one computer is connected to the network and uses the three ways handshake model to establish the connection which makes it more reliable.
2. What is the UDP protocol?
UDP is the User Datagram Protocol and is based on Datagrams. Mainly, it is used for multicasting and broadcasting. Its functionality is almost the same as TCP/IP Protocol except for the three ways of handshaking and error checking. It uses a simple transmission without any hand-shaking which makes it less reliable.
3. Compare TCP and UDP
4. What is the ICMP protocol?
ICMP is the Internet Control Message Protocol. It is a network layer protocol used for error handling. It is mainly used by network devices like routers for diagnosing network connection issues and is crucial for error reporting and testing if the data is reaching the preferred destination in time. It uses port 7 by default.
5. What do you mean by the DHCP Protocol?
DHCP is the Dynamic Host Configuration Protocol.
It is an application layer protocol used to auto-configure devices on IP networks enabling them to use TCP and UDP-based protocols. The DHCP servers auto-assign the IPs and other network configurations to the devices individually which enables them to communicate over the IP network. It helps to get the subnet mask, and IP address and helps to resolve the DNS. It uses port 67 by default.
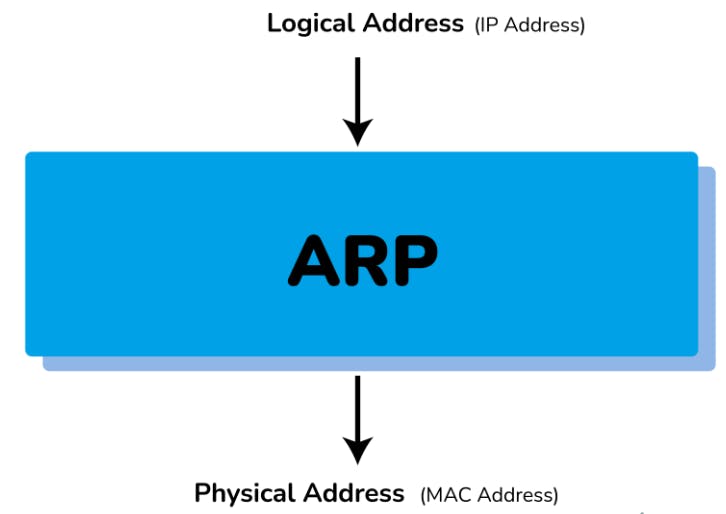
6. What is the ARP protocol?
ARP is Address Resolution Protocol. It is a network-level protocol used to convert the logical address i.e. IP address to the device's physical address i.e. MAC address. It can also be used to get the MAC address of devices when they are trying to communicate over the local network.
7. What is the FTP protocol?
FTP is a File Transfer Protocol. It is an application layer protocol used to transfer files and data reliably and efficiently between hosts. It can also be used to download files from remote servers to your computer. It uses port 27 by default.
8. What is the MAC address and how is it related to NIC?
MAC address is the Media Access Control address. It is a 48-bit or 64-bit unique identifier of devices in the network. It is also called the physical address embedded with Network Interface Card (NIC) used at the Data Link Layer. NIC is a hardware component in the networking device using which a device can connect to the network.
9. Differentiate the MAC address from the IP address
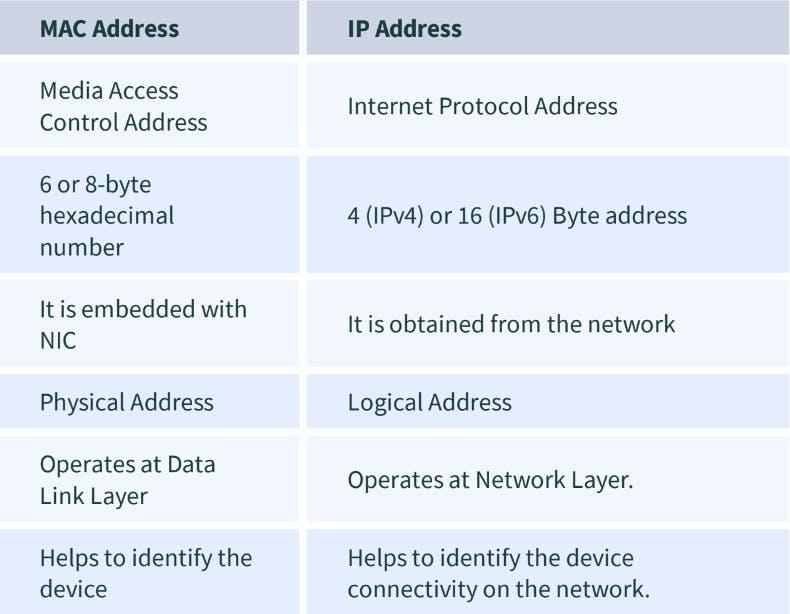
10. What is a subnet?
A subnet is a network inside a network achieved by the process called subnetting which helps divide a network into subnets. It is used for getting a higher routing efficiency and enhances the security of the network. It reduces the time to extract the host address from the routing table.
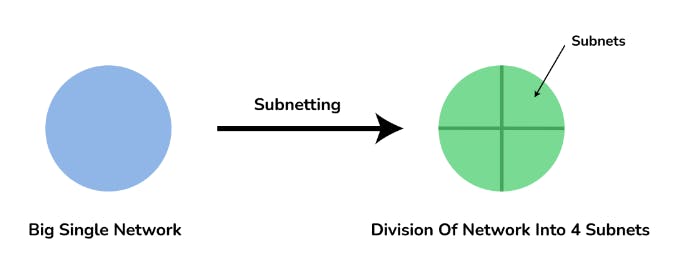
11. Compare the hub vs switch
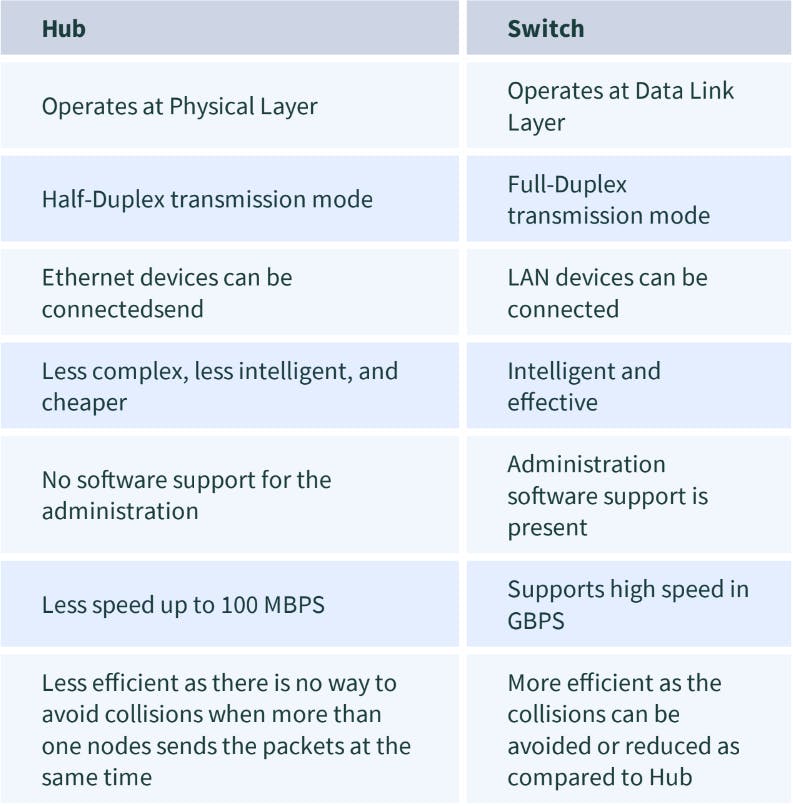
12. What is the difference between the ipconfig and the ifconfig?
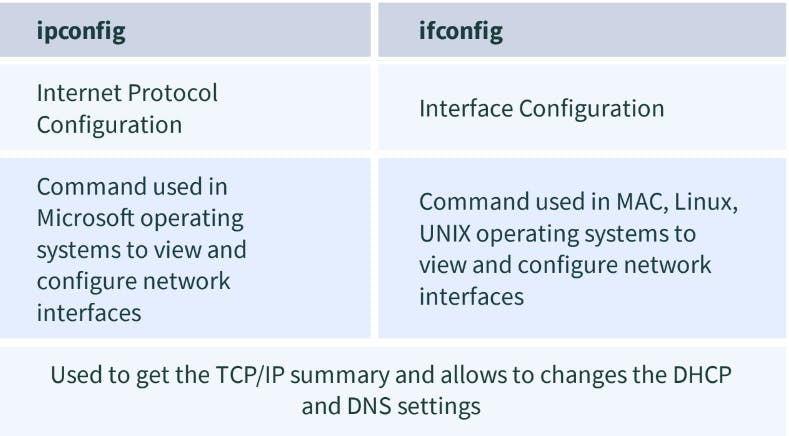
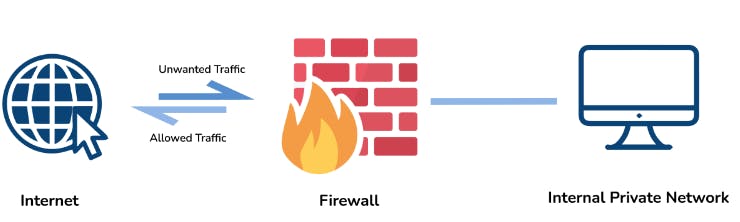
13. What is the firewall?
The firewall is a network security system that is used to monitor incoming and outgoing traffic and blocks the same based on firewall security policies. It acts as a wall between the internet (a public network) and the networking devices (a private network). It is either a hardware device, a software program, or a combination of both.
It adds a layer of security to the network.
14. What are Unicasting, Anycasting, Multicasting and Broadcasting?
Unicasting: If the message is sent to a single node from the source then it is known as unicasting. This is commonly used in networks to establish a new connection.
Anycasting: If the message is sent to any of the nodes from the source then it is known as anycasting. It is mainly used to get the content from any of the servers in the Content Delivery System.
Multicasting: If the message is sent to a subset of nodes from the source then it is known as multicasting. Used to send the same data to multiple receivers.
Broadcasting: If the message is sent to all the nodes in a network from a source then it is known as broadcasting. DHCP and ARP in the local network use broadcasting.
15. What happens when you enter google.com in the web browser?
Check the browser cache first if the content is fresh and present in the cache display the same.
If not, the browser checks if the IP of the URL is present in the cache (browser and OS) if not then request the OS to do a DNS lookup using UDP to get the corresponding IP address of the URL from the DNS server to establish a new TCP connection.
A new TCP connection is set between the browser and the server using three- way handshaking.
An HTTP request is sent to the server using the TCP connection.
The web servers running on the Servers handle the incoming HTTP request and send the HTTP response.
The browser process the HTTP response sent by the server and may close the TCP connection or reuse the same for future requests.
If the response data is cacheable then browsers cache the same.
The browser decodes the response and renders the content.
Conclusion
In today’s world, it is very hard to stay away from the Internet and that is what makes networking one of the most important interview topics. As of 2022 if we check the facts, there is a total of 1.3 million kilometers of submarine optical fiber cables set globally to connect the world to the Internet. These cables are more than enough to revolve around the earth more than 100 times.